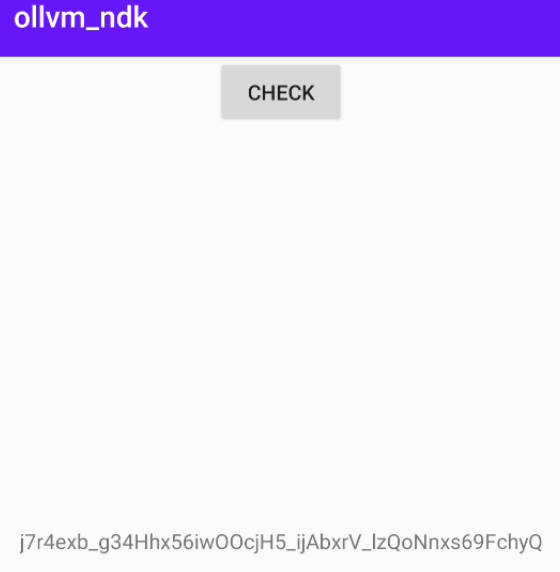
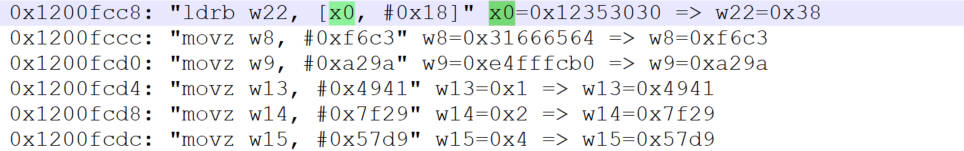ollvm9.apk
Jadx反编译分析
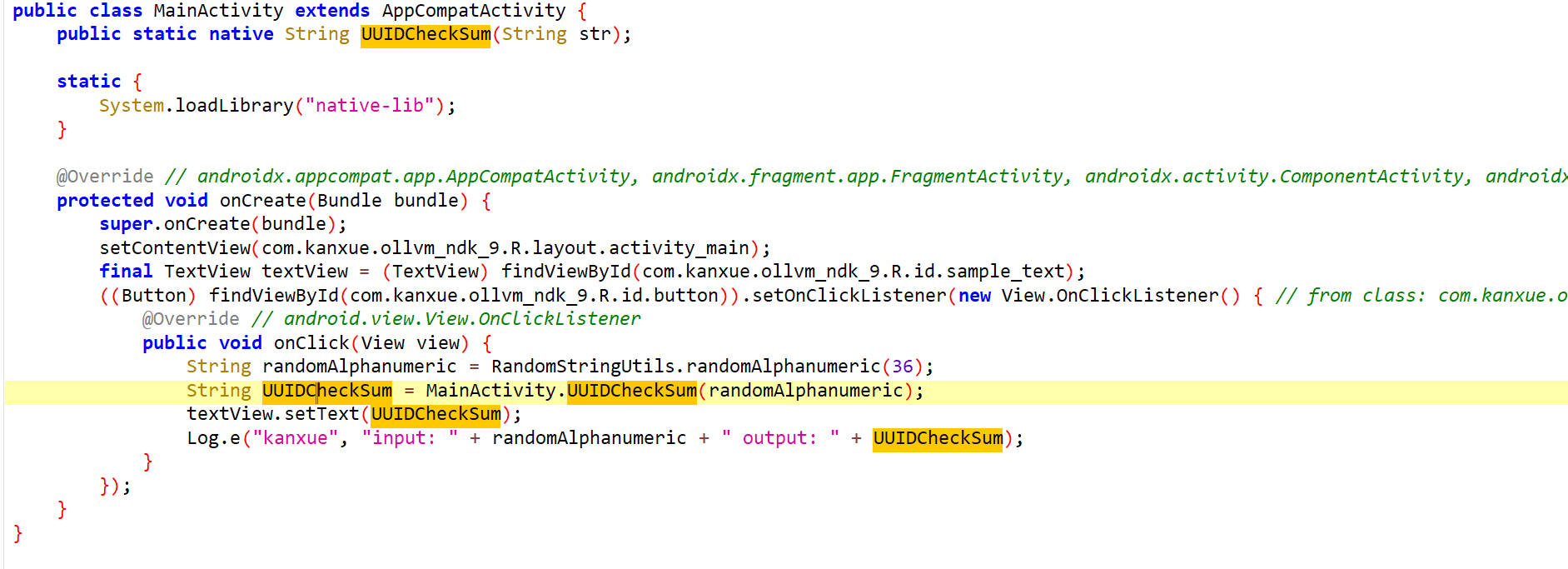
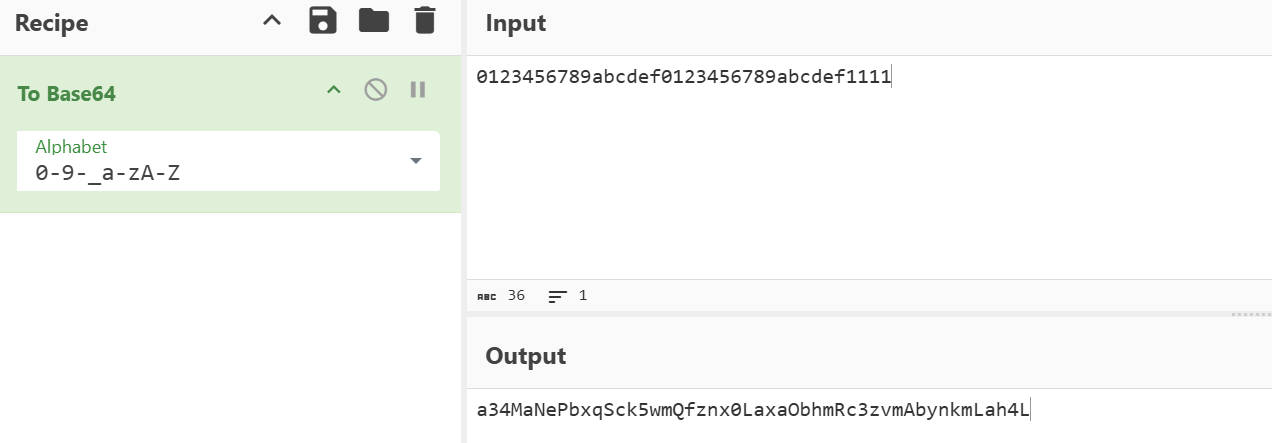
通过UUIDCheckSum()方法生成签名,参数是随机生成的长度36的字母数字字符串。
frida主动调用
1 2 3 4 5 6 7 8 function call_UUIDCheckSum ( Java .perform (function ( let MainActivity = Java .use ("com.kanxue.ollvm_ndk.MainActivity" ); let result = MainActivity .UUIDCheckSum ("0123456789abcdef0123456789abcdef1111" ); console .log ("result:" ,result); return result; }) }
结果
1 2 call_UUIDCheckSum() result: ah0NaxiObNmHc61xmwOOnN4K_h8Pb3qT_hvumQ9zn6qKa6aN
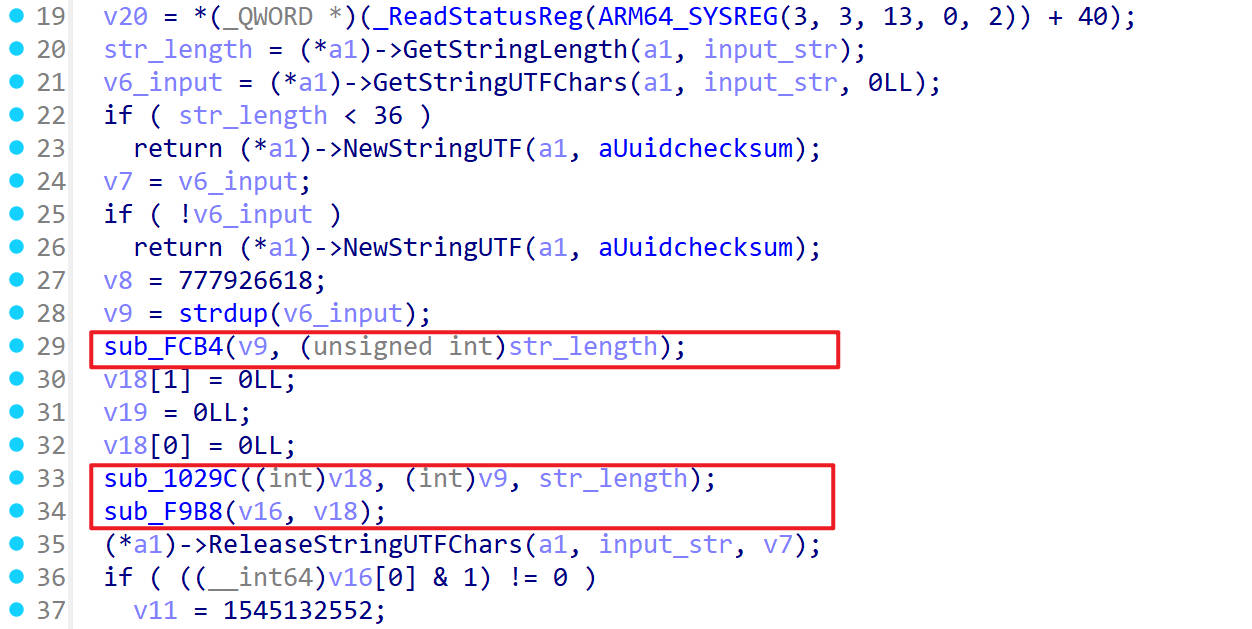
so分析 使用IDA打开so文件,跳转到UUIDCheckSum函数处
UUIDCheckSum函数里又调用了三个函数
hook_sub_FCB4() 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 function hook_sub_FCB4 ( let funcaddr = Module .findBaseAddress ("libnative-lib.so" ).add (0xFCB4 ); Interceptor .attach (funcaddr,{ onEnter :function (args ){ console .log ("arg0:" ,args[0 ].readCString ()); console .log ("arg1:" ,args[1 ]); this .arg0 = args[0 ]; }, onLeave :function ( console .log ("ret this.arg0:" ,this .arg0 .readCString ()); } }) } hook_sub_FCB4 ()
hook结果
1 2 3 arg0: 0123456789abcdef0123456789abcdef1111 arg1: 0x24 ret this.arg0: 10325476-8`cb-4g10-25479-8`cbedg00c3
hook_sub_1029C() 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 function hook_sub_1029C ( let funcaddr = Module .findBaseAddress ("libnative-lib.so" ).add (0x1029C ); Interceptor .attach (funcaddr,{ onEnter :function (args ){ console .log ("1029C arg0:" ,args[0 ].readCString ()); console .log ("1029C arg1:" ,args[1 ].readCString ()); console .log ("1029C arg2:" ,args[2 ]); this .arg0 = args[0 ]; this .arg1 = args[1 ]; }, onLeave :function ( console .log ("1029C ret this.arg0:" ,this .arg0 .readCString ()); console .log ("1029C ret this.arg1:" ,this .arg1 .readCString ()); } }) } hook_sub_1029C ()
hook结果,它被调用了两次,在其他地方也被调用了
1 2 3 4 5 6 7 8 9 10 11 1029C arg0: 1029C arg1: 10325476-8`cb-4g10-25479-8`cbedg00c3 1029C arg2: 0x24 1029C ret this.arg0: 1 1029C ret this.arg1: 10325476-8`cb-4g10-25479-8`cbedg00c3 1029C arg0: 1029C arg1: 10325476-8`cb-4g10-25479-8`cbedg00c3 1029C arg2: 0x24 1029C ret this.arg0: 1 1029C ret this.arg1: 10325476-8`cb-4g10-25479-8`cbedg00c3
hook_sub_F9B8() 1 2 3 4 5 6 7 8 9 10 11 12 13 14 function hook_sub_F9B8 ( let funcaddr = Module .findBaseAddress ("libnative-lib.so" ).add (0xF9B8 ); Interceptor .attach (funcaddr,{ onEnter :function (args ){ console .log ("F9B8 arg0:" ,args[0 ].readCString ()); this .arg0 = args[0 ]; }, onLeave :function ( console .log ("F9B8 ret this.arg0:" ,this .arg0 .readCString ()); } }) } hook_sub_F9B8 ()
hook 结果
1 2 F9B8 arg0: 1 F9B8 ret this.arg0: 1
这两个函数好像没有做什么事情
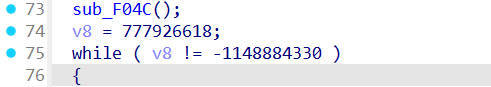
在函数F9B8()里看到还调用了其他函数
hook_sub_F04C() 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 function hook_sub_F04C ( let funcaddr = Module .findBaseAddress ("libnative-lib.so" ).add (0xF04C ); Interceptor .attach (funcaddr,{ onEnter :function (args ){ console .log ("F04C arg0:" ,args[0 ].readCString ()); console .log ("F04C arg1:" ,args[1 ]); console .log ("F04C arg2:" ,args[2 ]); console .log ("F04C arg3:" ,args[3 ]); console .log ("F04C arg4:" ,args[4 ].readCString ()); console .log ("F04C arg5:" ,args[5 ].readCString ()); }, onLeave :function (retval ){ console .log ("F04C ret:" ,retval); } }) } hook_sub_F04C ()
hook结果
1 2 3 4 5 6 7 F04C arg0: 10325476-8`cb-4g10-25479-8`cbedg00c3 F04C arg1: 0x24 F04C arg2: 0x24 F04C arg3: 0xdde4659c F04C arg4: F04C arg5: F04C ret: 0xfd39fea0
这里的两个地址无法访问
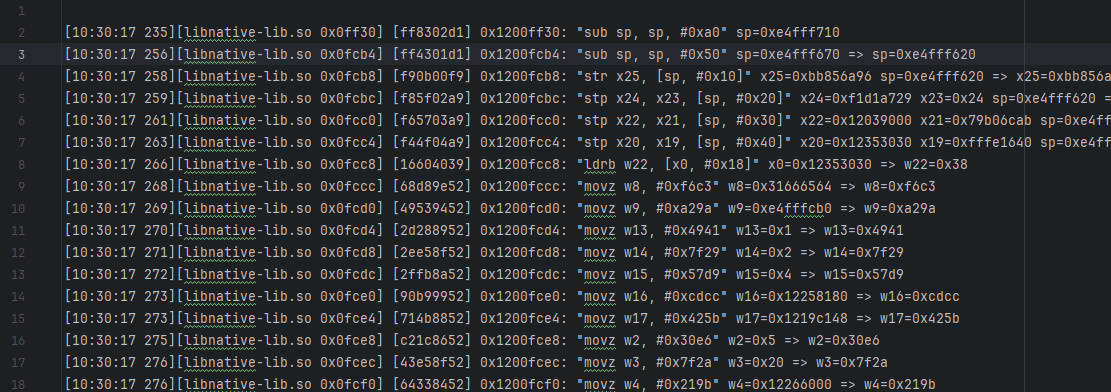
UnidbgTrace FCB4 先把函数模拟执行了,不需要补环境
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 public class MainActivity extends AbstractJni { private final AndroidEmulator emulator; private String process = "" ; private final Memory memory; private final VM vm; private DalvikModule dm; private Module module ; public MainActivity () { emulator = AndroidEmulatorBuilder .for64Bit() .setProcessName(process) .setRootDir(new File ("target/rootfs" )) .addBackendFactory(new Unicorn2Factory (true )) .build(); memory = emulator.getMemory(); memory.setLibraryResolver(new AndroidResolver (23 )); vm = emulator.createDalvikVM(new File ("apktest/ollvm9.apk" )); vm.setJni(this ); dm = vm.loadLibrary("native-lib" ,true ); dm.callJNI_OnLoad(emulator); module = dm.getModule(); } public String UUIDCheckSum () { DvmClass dvmClass = vm.resolveClass("com.kanxue.ollvm_ndk.MainActivity" ); StringObject stringObject = dvmClass.callStaticJniMethodObject(emulator,"UUIDCheckSum(Ljava/lang/String;)Ljava/lang/String;" ,"0123456789abcdef0123456789abcdef1111" ); return stringObject.getValue(); } public static void main (String[] args) { MainActivity main = new MainActivity (); System.out.println(main.UUIDCheckSum()); } }
在UUIDCheckSum()里添加trace代码
这里trace FCB4()函数的地址范围
1 2 3 4 5 6 7 8 9 String traceFile = "myTraceCodeFile_FCB4.txt" ;PrintStream traceStream = null ;try { traceStream = new PrintStream (new FileOutputStream (traceFile)); } catch (FileNotFoundException e) { throw new RuntimeException (e); } emulator.traceCode(0x1200FCB4 ,0x1200FCB4 +0x27C ).setRedirect(traceStream);
分析trace 使用notepad++助力分析日志文件
函数返回值会存放在X0寄存器里,找到它的地址
X0为0x12353030
搜索0x12353030,先分析一段数据
1 2 3 4 5 0x1200fe18: "ldrb w20, [x0, x22]" x0=0x12353030 x22=0x0 => w20=0x30 ;从x22加载一个字节到w20 0x1200fe1c: "ldrb w21, [sp, #0xc]" sp=0xe4fff620 => w21=0xff 0x1200fe20: "ldr w23, [sp, #0x1c]" sp=0xe4fff620 => w23=0x0 0x1200fe24: "eor w24, w20, #1" w20=0x30 => w24=0x31 ;w20与1异或后存入w24 0x1200fe28: "strb w24, [x0, x22]" w24=0x31 x0=0x12353030 x22=0x0 => w24=0x31 ;w24存入x22
我们传入的参数转16进制
1 2 0123456789abcdef0123456789abcdef1111 30 31 32 33 34 35 36 37 38 39 61 62 63 64 65 66 30 31 32 33 34 35 36 37 38 39 61 62 63 64 65 66 31 31 31 31
把FCB4()的返回值转为16进制
1 2 10325476-8`cb-4g10-25479-8`cbedg00c3 31 30 33 32 35 34 37 36 2d 38 60 63 62 2d 34 67 31 30 2d 32 35 34 37 39 2d 38 60 63 62 65 64 67 30 30 63 33
初步猜想通过异或处理的,用C语言实现一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 #include "stdio.h" #include "string.h" #include "stdlib.h" void sub_FCB4 (char * input,int length,char * result) { for (int i = 0 ; i < length; ++i) { unsigned char w20 = input[i]; unsigned char w24 = w20 ^ 1 ; result[i] = w24; } for (int i = 0 ; i < length; ++i) { printf ("%0x " ,result[i]); } } int main () { char *input = "0123456789abcdef0123456789abcdef1111" ; int length = strlen (input); int *result = (int *) malloc (length); sub_FCB4(input,length,result); return 0 ; }
这里输出结果与真实结果还是有差异的,对比分析
1 2 31 30 33 32 35 34 37 36 39 38 60 63 62 65 64 67 31 30 33 32 35 34 37 36 39 38 60 63 62 65 64 67 30 30 30 30 //输出结果 31 30 33 32 35 34 37 36 2d 38 60 63 62 2d 34 67 31 30 2d 32 35 34 37 39 2d 38 60 63 62 65 64 67 30 30 63 33 //真实结果
到trace中查找分析
发现如下这几种情况没有进行异或,而是直接传的固定的值
1 2 3 4 5 6 7 "strb w7, [x0, x20]" w7=0x2d x0=0x12353030 x20=0x8 => w7=0x2d "strb w7, [x0, x20]" w7=0x2d x0=0x12353030 x20=0xd => w7=0x2d "strb w7, [x0, x20]" w7=0x2d x0=0x12353030 x20=0x12 => w7=0x2d "strb w7, [x0, x20]" w7=0x2d x0=0x12353030 x20=0x18 => w7=0x2d "strb w6, [x0, x20]" w6=0x34 x0=0x12353030 x20=0xe => w6=0x34 "strb w8, [x0, #0x23]" w8=0x33 x0=0x12353030 => w8=0x33 "strb w8, [x0, #0x22]" w8=0x63 x0=0x12353030 => w8=0x63
重新使用C语言实现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 #include "stdio.h" #include "string.h" #include "stdlib.h" void sub_FCB4 (char * input,int length,char * result) { for (int i = 0 ; i < length; ++i) { unsigned char w20 = input[i]; if (i==0x8 || i==0xd || i==0x12 || i==0x18 ){ result[i] = 0x2d ; continue ; } if (i==0xe ){ result[i] = 0x34 ; continue ; } if (i==0x22 ){ result[i] = 0x63 ; continue ; } if (i==0x23 ){ result[i] = 0x33 ; continue ; } unsigned char w24 = w20 ^ 1 ; result[i] = w24; } for (int i = 0 ; i < length; ++i) { printf ("%0x " ,result[i]); } } int main () { char *input = "0123456789abcdef0123456789abcdef1111" ; int length = strlen (input); int *result = (int *) malloc (length); sub_FCB4(input,length,result); return 0 ; }
再次对比
1 2 31 30 33 32 35 34 37 36 2d 38 60 63 62 2d 34 67 31 30 2d 32 35 34 37 36 2d 38 60 63 62 65 64 67 30 30 63 33 // 输出结果 31 30 33 32 35 34 37 36 2d 38 60 63 62 2d 34 67 31 30 2d 32 35 34 37 39 2d 38 60 63 62 65 64 67 30 30 63 33 //真实结果
发现还是有一个地方不一样
到trace日志中查看
1 2 3 4 5 6 7 8 9 10 0x1200fcc8: "ldrb w22, [x0, #0x18]" x0=0x12353030 => w22=0x38 ... 0x1200fd44: "strb w22, [x0, #0x17]" w22=0x38 x0=0x12353030 => w22=0x38 ... 0x1200fe14: "ldrsw x22, [sp, #0x18]" x22=0x8f61219b sp=0xe4fff620 => x22=0x17 0x1200fe18: "ldrb w20, [x0, x22]" x0=0x12353030 x22=0x17 => w20=0x38 0x1200fe1c: "ldrb w21, [sp, #0xc]" sp=0xe4fff620 => w21=0xc5 0x1200fe20: "ldr w23, [sp, #0x1c]" sp=0xe4fff620 => w23=0x494 0x1200fe24: "eor w24, w20, #1" w20=0x38 => w24=0x39 0x1200fe28: "strb w24, [x0, x22]" w24=0x39 x0=0x12353030 x22=0x17 => w24=0x39
修改C
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 #include "stdio.h" #include "string.h" #include "stdlib.h" void sub_FCB4 (char * input,int length,char * result) { for (int i = 0 ; i < length; ++i) { if (i==0x8 || i==0xd || i==0x12 || i==0x18 ){ result[i] = 0x2d ; continue ; } if (i==0xe ){ result[i] = 0x34 ; continue ; } if (i==0x22 ){ result[i] = 0x63 ; continue ; } if (i==0x23 ){ result[i] = 0x33 ; continue ; } if (i==0x17 ){ result[i]=input[i+1 ] ^1 ; continue ; } unsigned char w20 = input[i]; unsigned char w24 = w20 ^ 1 ; result[i] = w24; } for (int i = 0 ; i < length; ++i) { printf ("%0x " ,result[i]); } } int main () { char *input = "0123456789abcdef0123456789abcdef1111" ; int length = strlen (input); int *result = (int *) malloc (length); sub_FCB4(input,length,result); return 0 ; }
这次的结果就与真实结果是一样的
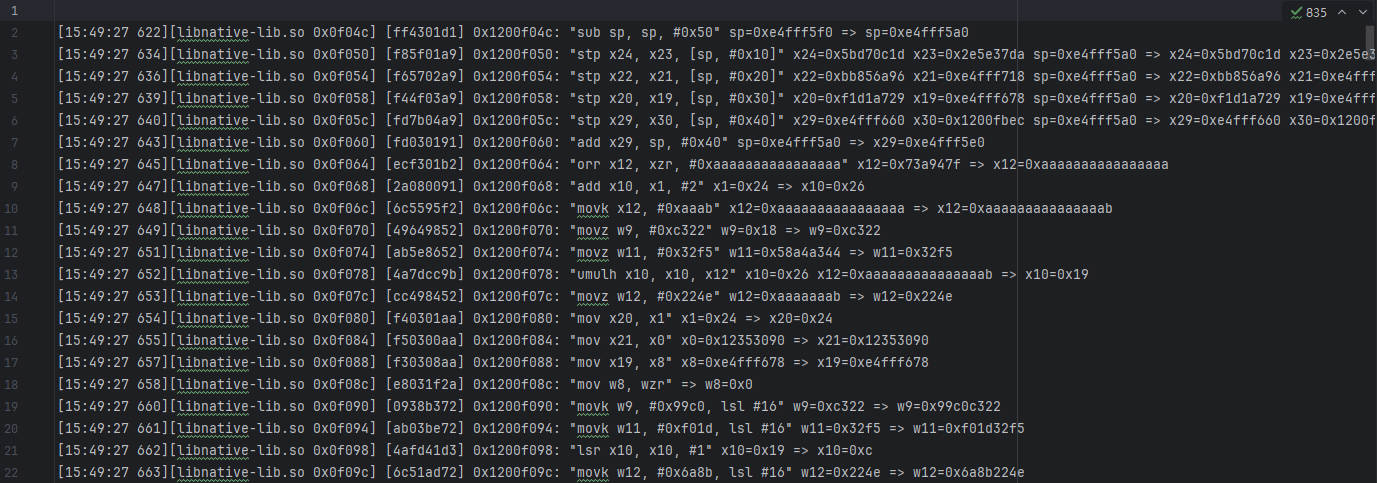
UnidbgTrace F04C 修改trace代码
1 2 3 4 5 6 7 8 9 String traceFile = "myTraceCodeFile_F04C.txt" ;PrintStream traceStream = null ;try { traceStream = new PrintStream (new FileOutputStream (traceFile)); } catch (FileNotFoundException e) { throw new RuntimeException (e); } emulator.traceCode(0x1200F04C ,0x1200F04c +0x224 ).setRedirect(traceStream);
把返回值转为16进制
1 2 ah0NaxiObNmHc61xmwOOnN4K_h8Pb3qT_hvumQ9zn6qKa6aN 61 68 30 4e 61 78 69 4f 62 4e 6d 48 63 36 31 78 6d 77 4f 4f 6e 4e 34 4b 5f 68 38 50 62 33 71 54 5f 68 76 75 6d 51 39 7a 6e 36 71 4b 61 36 61 4e
搜索x0,跳转到最开始的x0的地址0x12353090
然后搜索0x12353090
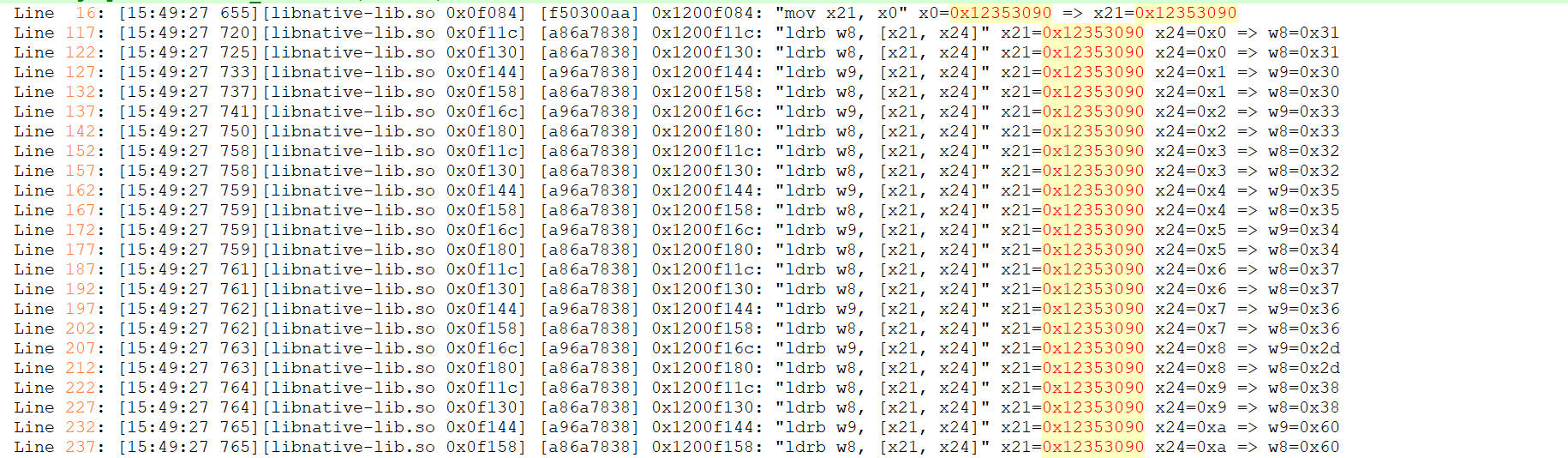
分析第一个值
1 2 3 4 5 6 7 8 9 "ldrb w8, [x21, x24]" x21=0x12353090 x24=0x0 => w8=0x31 "lsr x8, x8, #2" x8=0x31 => x8=0xc "ldrb w1, [x23, x8]" x23=0x12037010 x8=0xc => w1=0x61 "ldrb w8, [x21, x24]" x21=0x12353090 x24=0x0 => w8=0x31 1.把地址0x12353090偏移0x0处的值放入w8,w8=0x31 2.将寄存器x8里的值逻辑右移2位,x8=0xc 3.把地址0x12037010偏移为0xc处的值存入w1,w1=0x61 4.把地址0x12353090偏移0x0处的值再次放入w8,w8=0x31
这里出现的0x12037010这个地址指向的应该是一个表
用unidbg来找这个表,在函数地址0xF04C处下断点
1 emulator.attach().addBreakPoint(dm.getModule().base+0x0FF30 );
运行起来之后,用m0x12037010查看改地址处的数据为0123456789-_abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ
用C语言实现这个过程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 #include "stdio.h" #include "string.h" #include "stdlib.h" void sub_FCB4 (char * input,int length,char * result) { for (int i = 0 ; i < length; ++i) { if (i==0x8 || i==0xd || i==0x12 || i==0x18 ){ result[i] = 0x2d ; continue ; } if (i==0xe ){ result[i] = 0x34 ; continue ; } if (i==0x22 ){ result[i] = 0x63 ; continue ; } if (i==0x23 ){ result[i] = 0x33 ; continue ; } if (i==0x17 ){ result[i]=input[i+1 ] ^1 ; continue ; } unsigned char w20 = input[i]; unsigned char w24 = w20 ^ 1 ; result[i] = w24; } } void sub_F04C (char * input,int length,char * char_table,char *result) { for (int i = 0 ; i < length; ++i) { int x8 = input[i]>>2 ; result[i] = char_table[x8]; } for (int i = 0 ; i < length; ++i) { printf ("%0x " ,result[i]); } } int main () { char *input = "0123456789abcdef0123456789abcdef1111" ; int input_length = strlen (input); int *FCB4_result = (int *) malloc (input_length); sub_FCB4(input,input_length,FCB4_result); char *char_table = "0123456789-_abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ" ; char *F04C_result = (int *) malloc (48 ); sub_F04C(FCB4_result,48 ,char_table,F04C_result); return 0 ; }
与真实答案对比
1 2 61 61 61 61 62 62 62 62 5f 63 6d 6d 6d 5f 62 6e 61 61 5f 61 62 62 62 63 5f 63 6d 6d 6d 6e 6e 6e 61 61 6d 61 30 30 30 30 // 输出 61 68 30 4e 61 78 69 4f 62 4e 6d 48 63 36 31 78 6d 77 4f 4f 6e 4e 34 4b 5f 68 38 50 62 33 71 54 5f 68 76 75 6d 51 39 7a 6e 36 71 4b 61 36 61 4e // 真实结果
第一位是相同的,但是后面的还要继续分析
1 2 3 4 5 6 7 8 9 "ldrb w9, [x21, x24]" x21=0x12353090 x24=0x1 => w9=0x30 "orr x8, x8, x9, lsr #4" x8=0x10 x9=0x30 => x8=0x13 0x1200f14c: "ldrb w1, [x23, x8]" x23=0x12037010 x8=0x13 => w1=0x68 "ldrb w8, [x21, x24]" x21=0x12353090 x24=0x1 => w8=0x30 1.把0x12353090地址偏移为1处的值加载到w9寄存器里 2.将 x9 的值逻辑右移 4 位后,与 x8 的值按位或(OR),结果存回 x8,这里的x8来源于上次计算的结果 3.把地址0x12037010偏移为0x13处的值存入w1,w1=0x68 4.把0x12353090地址偏移为1处的值加载到w8寄存器里
往后看第三个参数和第四个参数
1 2 3 4 5 6 7 8 9 10 11 12 0x1200f16c: "ldrb w9, [x21, x24]" x21=0x12353090 x24=0x2 => w9=0x33 # 从地址(x21 + x24)加载一个字节到w9 0x1200f170: "orr x8, x8, x9, lsr #6" x8=0x0 x9=0x33 => x8=0x0 # 将w9右移6位后与x8进行OR操作 0x1200f174: "ldrb w1, [x23, x8]" x23=0x12037010 x8=0x0 => w1=0x30 # 从地址(x23 + x8)加载一个字节到w1 0x1200f180: "ldrb w8, [x21, x24]" x21=0x12353090 x24=0x2 => w8=0x33 # 从地址(x21 + x24)加载一个字节到w8 0x1200f184: "and x8, x8, #0x3f" x8=0x33 => x8=0x33 # 把x8同0x3f进行与操作,结果放入x8 0x1200f188: "ldrb w1, [x23, x8]" x23=0x12037010 x8=0x33 => w1=0x4e # 从地址(x23 + x8)加载一个字节到w1 0x1200f11c: "ldrb w8, [x21, x24]" x21=0x12353090 x24=0x3 => w8=0x32 # 从地址(x21 + x24)加载一个字节到w8 0x1200f120: "lsr x8, x8, #2" x8=0x32 => x8=0xc # 将x8右移2位 0x1200f124: "ldrb w1, [x23, x8]" x23=0x12037010 x8=0xc => w1=0x61 # 从地址(x23 + x8)加载一个字节到w1
猜测这是循环操作的,每三个是一组,每组后面会加一步操作添加一个数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 #include "stdio.h" #include "string.h" #include "stdlib.h" void sub_FCB4 (char * input,int length,char * result) { for (int i = 0 ; i < length; ++i) { if (i==0x8 || i==0xd || i==0x12 || i==0x18 ){ result[i] = 0x2d ; continue ; } if (i==0xe ){ result[i] = 0x34 ; continue ; } if (i==0x22 ){ result[i] = 0x63 ; continue ; } if (i==0x23 ){ result[i] = 0x33 ; continue ; } if (i==0x17 ){ result[i]=input[i+1 ] ^1 ; continue ; } unsigned char w20 = input[i]; unsigned char w24 = w20 ^ 1 ; result[i] = w24; } } void sub_F04C (char * input,int length,char *result) { char *char_table = "0123456789-_abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ" ; int x8; int count =0 ; for (int i = 0 ; i < length; ++i) { if (i%3 ==0 ){ x8 = input[i]>>2 ; result[count] = char_table[x8]; count++; x8 = input[i]; } if (i%3 ==1 ){ x8 = ((x8&0b11 )<<4 ); x8 = (input[i]>>4 )^x8; result[count] = char_table[x8]; count++; x8 = input[i]; } if (i%3 ==2 ){ x8 = ((x8&0b1111 )<<2 ); x8 = (input[i]>>6 )^x8; result[count] = char_table[x8]; count++; x8 = input[i]; result[count] = char_table[x8&0x3f ]; count++; } } for (int i = 0 ; i < 48 ; ++i) { printf ("%0x " ,result[i]); } } int main () { char *input = "0123456789abcdef0123456789abcdef1111" ; int input_length = strlen (input); char *FCB4_result = (char *) malloc (input_length); sub_FCB4(input,input_length,FCB4_result); char *F04C_result = (char *) malloc (48 ); sub_F04C(FCB4_result,input_length,F04C_result); free (FCB4_result); free (F04C_result); return 0 ; }
1 2 61 68 30 4e 61 78 69 4f 62 4e 6d 48 63 36 31 78 6d 77 4f 4f 6e 4e 34 4b 5f 68 38 50 62 33 71 54 5f 68 76 75 6d 51 39 7a 6e 36 71 4b 61 36 61 4e // 输出内容 61 68 30 4e 61 78 69 4f 62 4e 6d 48 63 36 31 78 6d 77 4f 4f 6e 4e 34 4b 5f 68 38 50 62 33 71 54 5f 68 76 75 6d 51 39 7a 6e 36 71 4b 61 36 61 4e // 真实结果
根据这个运算过程,可以猜测它是base64了
最终确定它是魔改的base64